
National Cyber Security Awareness Month: Focus on People
This year’s National Cyber Security Month focuses on the human element of cybersecurity. We love that because PEOPLE are a vital part of your technology stack. When security teams are more prepared and confident, organizations benefit from an improved security posture and measurably reduced risk.

Helping CISOs Avoid Burnout and Reduce Risk
The CISO role is vital. The recent 2022 Global Chief Information Security Officer (CISO) Survey shows that CISO salaries have increased, which reflects their value and higher profile in their organizations. But CISOs are at risk of burnout. Cloud Range can help.
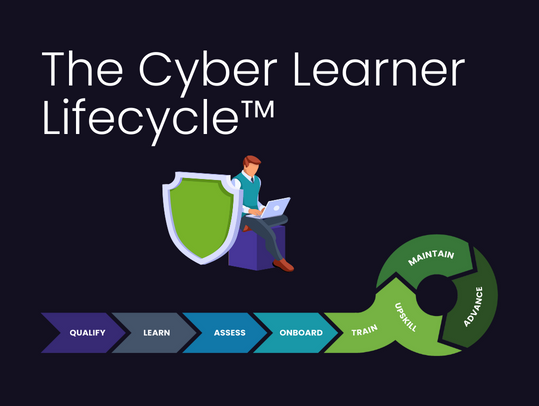
The Cyber Learner Lifecycle™
The Cyber Learner Lifecycle™ covers all the stages for learning and training that a cybersecurity professional goes through, including everything that happens before employment, as they're employed, and throughout their career.
![CISOs Look To Bake Simulation Into Cyber Defense [Cybercrime Magazine]](https://images.squarespace-cdn.com/content/v1/622a4857d0e0ed54ed5da4ce/1659971801277-N1ZCUZOWVZALXJG8BAEM/cisos-image.jpg)
CISOs Look To Bake Simulation Into Cyber Defense [Cybercrime Magazine]
The bad guys are going to be one step ahead — as we hear about in the news every day — and CISOs have to acknowledge that everything is not going to be secure. CISOs should include simulation in cyber defense to help their teams do as much as they can to stay ahead of what is yet to come.

Using a Cyber Range to Hire & Train an Awesome SOC Team
The cybersecurity industry has a conundrum. It’s hard to find and vet top-notch SOC analysts and then train them into a successful, collaborative team. Good news: There are cyber range solutions that can help.

Five Questions Senior Executives Should Ask CISOs About Training
Cybersecurity has emerged as an important component of the conversations that occur at the senior executive and board levels. Furthermore, it is no longer uncommon for boards and leadership teams to include at least one member who has some experience in this critically important area. To address this issue, we offer below five questions that senior executives should ask their Chief Information Security Officer (CISO).

Using Cyber Simulation to Improve OT/ICS Security
Security teams need to understand not only traditional cybersecurity tactics and procedures, but also OT-specific ones. Cyber simulation exercises designed expressly for OT/ICS security help cyber defenders be more effective and reduce risk.

How Are Cybersecurity and Baseball Alike?
Similar to baseball, cyber defense is a team sport. While baseball practice gets teams game-ready, cybersecurity simulation practice gets security teams battle-ready. Either way, improving knowledge, skills and abilities ensures you can knock it out of the park.

Cybersecurity Awareness for Employees: Best Practices - IT Business Edge Article
Cloud Range Founder & CEO Debbie Gordon was featured in the IT Business Edge article Cybersecurity Awareness for Employees: Best Practices for her thoughts on how simulation can be leveraged in protecting a company against the inevitable cyber attack.

What is Log4j, why is everyone talking about it, and what do you need to do NOW?
Log4Shell as a concept is much easier to explain when you don’t need to identify where this (nearly ubiquitous) library has been used in a given app or service.

Cloud Range to Provide Cyber Simulation Training for Booz Allen Hamilton Employees
Cloud Range announced today that it has been selected to participate in Booz Allen Hamilton’s FlexEd program, an enhanced, continuing education benefit for the firm’s 27,000+ employees.

Cloud Range in Cybercrime Magazine: Cybersecurity And The Super Bowl: What CISOs Should Know
Despite industry-wide efforts to reduce the skills gap, the 3.5 million unfilled cybersecurity jobs in 2021 will be enough to fill 50 NFL stadiums.

Results of a SOC Simulation Training Survey
Every enterprise security team, regardless of size, scope, or sector, knows the value of having a capable and well-trained Security Operations Center (SOC) team addressing their cyber threats. Larger companies often have the budget to recruit and employ their own SOC team, whereas others will tend to hire an externally-managed SOC team, often through a managed security service provider (MSSP).
