Cloud Range’s Cyber Range Resources
Cloud Range provides a wide range of free resources, including webinars, data sheets, ebooks, and case studies. Our resources are full of great information regarding cyber ranges, industry trends, and Cloud Range solutions.

Dive into this exclusive eBook by TAG Infosphere to explore how simulation-based training, AI integration, and human-first frameworks are redefining cyber readiness.
Your SOC’s Secret Weapon: Real-World Simulation
Not Your Momma’s Tabletop Exercise! Triple the Impact with Half the Effort
Transform tabletop exercises with actionable plans and AI integration. Simplify compliance, streamline design, and measure true impact and value.
NICE Success Story: Cloud Range
Cloud Range’s live-fire simulations and labs align with the NICE Framework, enabling focused skill development and custom learning paths. This setup boosts proficiency, identifies gaps, and supports career growth, offering clear metrics for cybersecurity professionals.
Commanding the Front Lines:
5 Crucial Techniques of Effective Cybersecurity Incident Commanders
Incident Commanders can make or break an outcome. This webinar and panel discussion will help you ensure they are equipped for effective incident response.
Analysis of Volt Typhoon Attack: A Discussion on Securing Critical Infrastructure
Learn more about this attack and other threats to critical infrastructure, and gain insights to minimize risk and bolster cyber resilience.
Anatomy of an Industrial Attack Webinar
Dive into a real-life OT cyber attack on a water treatment plant — learn how it happened, what was exploited, and how to minimize and remediate incidents affecting cyber-physical systems.
Cloud Range Cybersecurity Incident Commander Training Data Sheet
Cloud Range Cybersecurity Incident Commander Training is designed especially for new or prospective Incident Commanders interested in developing skills to help them lead an incident response team.
Global Communications Company Case Study
This case study illustrates the significant enhancement of incident response time and preparedness achieved by the Security Operations Center (SOC) team of a leading Global Telecommunications Company through the implementation of Cloud Range's Attack Simulation Training Program.
Cloud Range’s red team vs. blue team exercises are live-fire cyber attack simulations on a virtual, dynamic cyber range. The exercises will help you fortify your cybersecurity posture, verify compliance, improve team collaboration, and train teams for red vs blue competitions.
Red Team vs. Blue Team Data Sheet
Cloud Range’s core solution, FlexRange™ Live-Fire Cyber Attack Simulation Training, is a full-service program of
immersive, simulation-based training missions and lab exercises.
FlexRange Data Sheet
See Range365 in action through a live demo. Experience the ability to seamlessly work with IT and OT/ICS environments while harnessing a variety of powerful tools to address real-world challenges.
Introducing Range365: A New Generation of Advanced Cyber Ranges
Introducing the Industry's Only OT Cyber Range for Live-Fire Training: Conquer OT Attacks in an IT-Focused World
Learn how realistic simulation training minimizes cyber risk in the IT/OT threat landscape. This 60-minute webinar includes a demo of the only OT cyber range for live-fire training.
The Future of SOC Readiness and Cyber Resilience
Learn about insights, observations, and predictions on the current state and future prospects of SOC cyber readiness programs and how to reduce risk for the whole organization.
This 30-minute webinar outlines the 5 most impactful ways that top enterprise security leaders are using cyber ranges and simulation to improve their security posture.
RightTrak maps each candidate’s natural talents and abilities with optimal cybersecurity roles, allowing you to easily identify top talent and put the right people in the right seats.
Cloud Range FlexLabs are sets of tutorial-based exercises that focus on specific knowledge and skill sets. The realistic environments and exercises give your team the hands-on experience needed for today’s threat landscape.
The Cloud Range RightTrak™ Cyber Aptitude Assessment identifies an individual's cognitive aptitude for a career in cybersecurity and matches their innate talents and abilities with their optimal cyber work role.
Cloud Range’s FastTrak Candidate Assessment tool objectively determines a candidate’s qualifications, practical skills, relative overall experience, and readiness to defend as a cybersecurity professional.
The Cyber Learner Lifecycle™ covers all the stages for learning and training that a cybersecurity professional goes through, including everything that happens before employment, as they're employed, and throughout their career.
Download eBook
Learn more about Cloud Range, our unique cyber range-as-a-service platform, and our comprehensive and customizable breadth of cyber readiness solutions. Ensure you are ready for today’s threats and reduce your cyber risk.
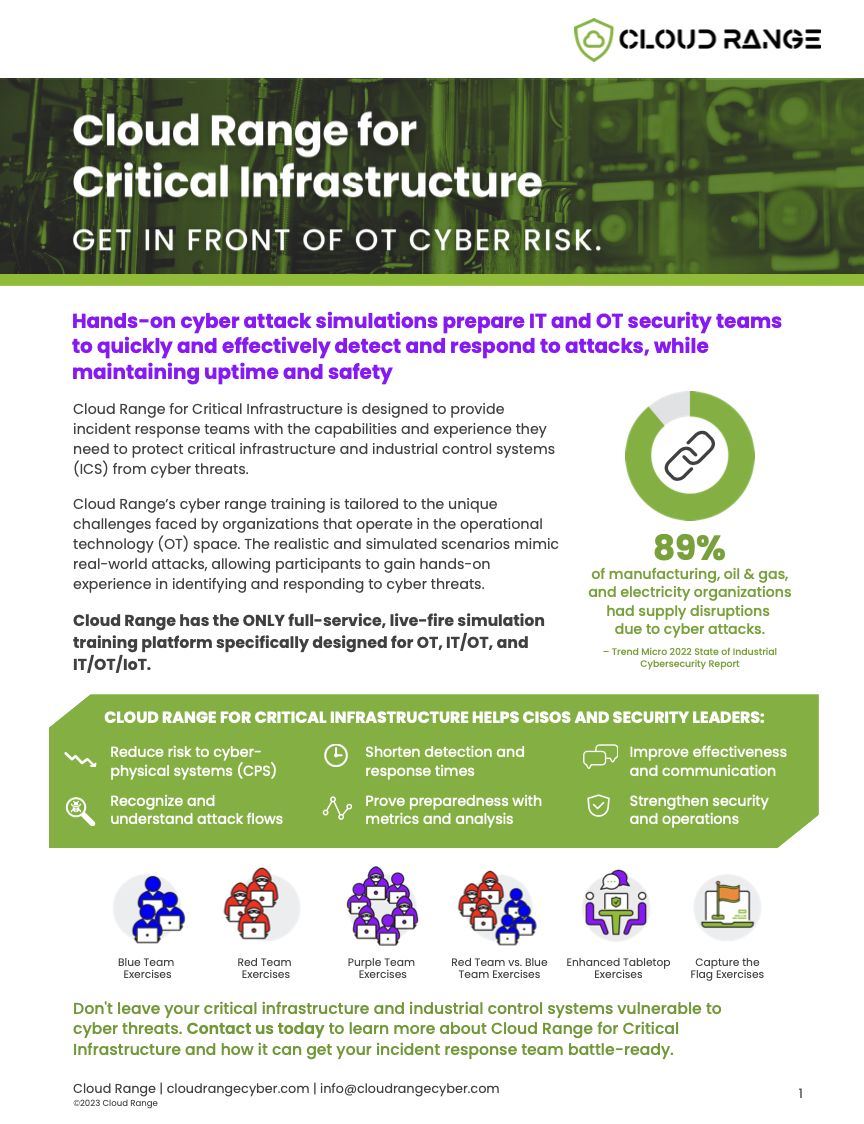
Cloud Range for Critical Infrastructure (OT) Data Sheet
Cloud Range for Critical Infrastructure is designed to provide incident response teams with the knowledge and skills they need to protect critical infrastructure and industrial control systems (ICS) from cyber threats.
Cloud Range Performance Portal Data Sheet
Cloud Range’s Performance Portal is the central hub for attack simulations, skills development courses, assessments, learning plans, detailed reporting, management and more. Learn how it will help you plan, implement, train, and assess your security teams.
This case study details how MSSP CyberMaxx used Cloud Range to onboard, train, and retain its SOC and IR teams — and how that positively impacted multiple areas of the organization.
This webinar looks at the changing roles of security leaders – which now includes talent management. We examine new ways for enterprise security leaders to optimize hiring and retention.
Empowering Students to Succeed in the Cybersecurity Job Market
This 30-minute webinar discusses how experiential learning equips cybersecurity students with hands-on training – bridging the gap between formal education and employability.
Cloud Range EDU™ Data Sheet
Cloud Range EDU helps institutions provide students with hands-on, experiential cybersecurity learning activities that increase skills, build confidence, and improve job placement.
Demystifying the NICE Framework Webinar
The NICE Framework delineates work roles and skills in cybersecurity. Its purpose is to provide a consistent definition of cybersecurity roles and requirements, fostering clearer communication and better role alignment across the industry.
Watch the Webinar
5 Reasons Your SOC Should Be Using Cyber Range Training Now
This ebook from leading industry research firm TAG Cyber focuses on why SOC teams should engage in regular cyber range training to simulate live-fire incidents, measure and reduce risk, and improve individual and team effectiveness.
Download eBook
Range365 Customized, Hosted Cyber Range Data Sheet
Range365 is the industry’s leading, enterprise-grade, hosted cyber range solution. It provides organizations with a training and testing ground for product demos, integration testing, live-fire cyber attack exercises, and more.
This ebook will help you transform your approach to talent management. Leverage the NICE Framework to bridge the skills gap, reduce turnover, and build a robust defense against cyber threats.
Demystifying The NICE Framework
Download eBook
Take traditional tabletop exercises to a new level with Cloud Range's holistic, comprehensive, and cross-disciplinary approach to detection, response, and remediation.
Tabletop 2.0 Data Sheet
State of Florida ISM-CSIRT Event Case Study
Discover how the State of Florida transformed its cybersecurity response with Cloud Range’s comprehensive cyber preparedness solution.
Nebraska National Guard Cyber Tatanka Case Study
The Nebraska National Guard partnered with Cloud Range to deliver advanced cyber defense training using live-fire simulations. Learn how Cloud Range's scalable Virtual Threat Environment helped improve incident response and foster collaboration across military, government, and civilian organizations.
Cyber Range Buyer’s Guide from TAG Infosphere
Choosing the right cyber range can be a game-changer for your security team. This Cyber Range Buyer’s Guide provides the roadmap to making the best decision, with key questions to evaluate solutions, content, and ROI.
Election Cyber Security:
5 Ways to Minimize the Risk of a Cyber Attack
Explore various attack vectors affecting election infrastructure and cyber security. Learn how to detect and remediate threats and ensure you are prepared for upcoming elections.
Perspectives on Establishing ICS/OT Cyber Resilience
This exclusive ebook from TAG Infosphere emphasizes the importance of combining security practices with teamwork between IT and operational technology teams. This approach helps organizations strengthen their defenses and improve their ability to recover from cyber incidents.
Beyond the Stack: Why Cyber Readiness Starts with People
Learn how leading organizations are building cyber resilience through people-first strategies, proactive training, and simulation-based preparation. Gain insights to strengthen your defenses and stay ahead of evolving threats.
From Simulation to Real Action: Cyber Readiness Lessons from the Front Lines in Healthcare
Move beyond compliance with live-fire cyber simulations. Learn how healthcare teams build instinct, speed response, and prove real-world readiness.
Watch Webinar