Creating an ICS/OT Cyber Incident Response Plan
Creating an ICS/OT Cyber Incident Response Plan
Dave Neuman
Senior Analyst, TAG Infosphere
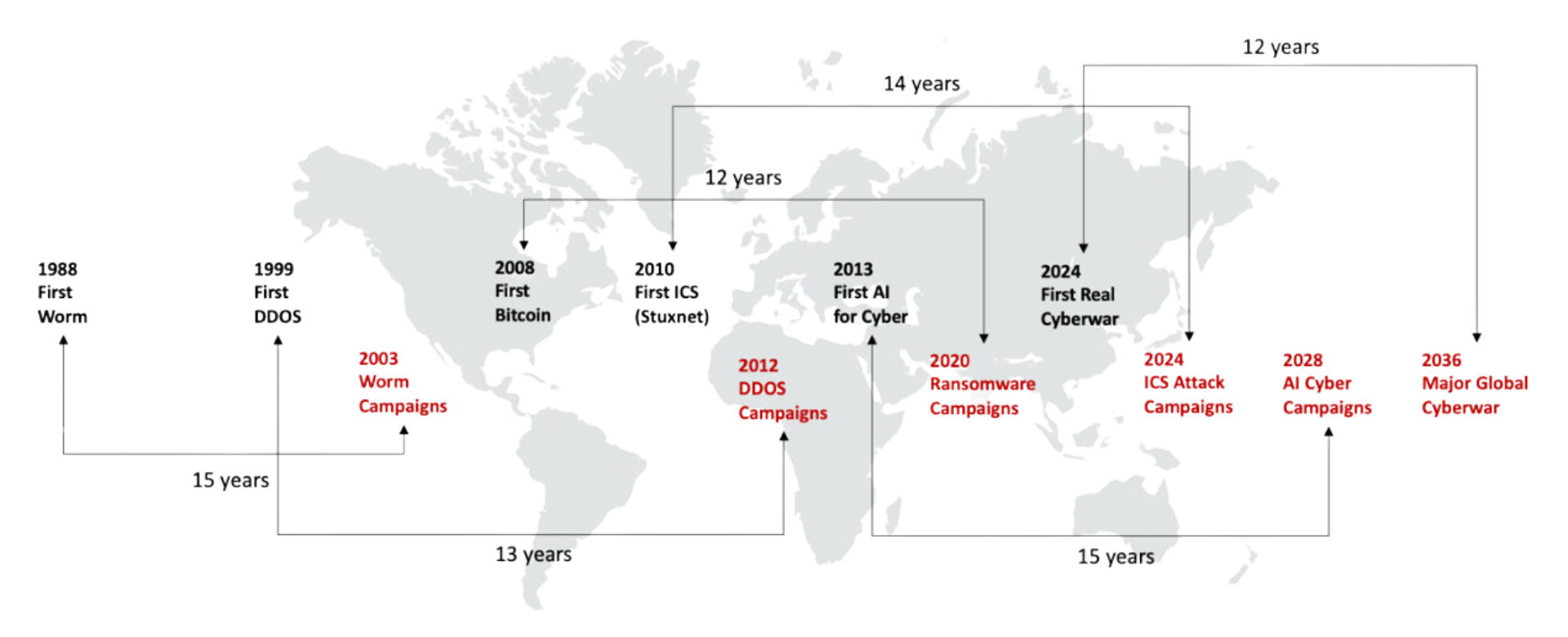
In 2022, TAG published an analysis using time patterns to predict cyber campaigns. By extrapolating the average time between initial cyber skirmishes and their corresponding full-out attack campaigns, predictions can be made about future attacks. The first serious ICS attack of any consequence occurred in 2010 with the Stuxnet incident, which targeted Iranian nuclear systems.
One can thus extrapolate that a series of ICS attacks should occur soon.
Figure 1. Future Attack Model Predicts ICS Campaigns
In 2022, the Kryvorizka power plant in Ukraine faced a combined kinetic and cyber attack. Russian missile strikes were complemented by an attempted cyber attack by the threat group XakNet on the plant's OT network. The attack aimed to destabilize the grid but ultimately failed.
From 2021-2023, Chinese state-sponsored threat actors targeted the Indian power grid by leveraging IoT devices such as vulnerable IP cameras to gain access to critical networks.
These examples demonstrate that ICS/OT systems are not only on the cyberattack target list but also that the attackers targeting these systems include some of the most highly skilled and resourced threats. In addition, ICS/OT systems are part of critical infrastructure that underpins businesses, governments, and society and pose a real risk of severe material damage and human lives.
It should come as no surprise that they would be attractive targets.
Addressing ICS/OT Challenges
One of the primary challenges in ICS/OT incident response is integrating the corresponding IT and OT systems. This convergence brings complexities due to differing priorities and technologies. IT systems prioritize data confidentiality and integrity, while OT systems are designed for continuous, reliable operation, emphasizing availability and physical safety.
Balancing these objectives is complex, as changes to IT can directly impact OT. Maintaining operational continuity while ensuring security is a delicate task during incident response. In ICS/OT environments, abrupt changes or shutdowns can disrupt critical processes, sometimes causing safety risks or financial losses.
Incident response teams must carefully assess and mitigate threats without unnecessarily halting operations, which requires understanding of the operational context and the potential impacts of security measures.
Another significant challenge is the need for ICS/OT-specific security tools and skilled professionals. The specialized nature of ICS/OT systems means that generic IT security solutions may need to be more effective and applicable, and there is a need for tools specifically designed for these environments.
Furthermore, there is a shortage of professionals with combined knowledge of cybersecurity, ICS technologies, and the specific operational processes of the industry in question. This gap makes detecting, analyzing, and responding to incidents in ICS/OT settings difficult, necessitating targeted training and recruitment strategies to build a capable workforce.
Developing an ICS/OT Response Plan
Developing a robust Incident Response Plan for ICS/OT is more crucial than ever in an interconnected and increasingly cyber-threatened world. An effective response plan is not just a set of procedures for responding to incidents but a comprehensive framework that ensures resilience, quick recovery, and minimal impact on operations.
The unique characteristics of ICS/OT, such as their critical role in infrastructure and reliance on legacy systems, necessitate a specialized approach to incident response. This approach must prioritize both these systems' security and continuous, safe operation.
The key elements of an ICS/OT Incident Response Plan encompass preparation, identification, containment, eradication, recovery, and lessons learned. Each element plays a vital role in addressing the specific challenges posed by cyber threats in ICS/OT environments:
Preparation: A well-prepared team is the foundation of an effective ICS/OT incident response plan. It is crucial to establish a cross-functional incident response team that includes members with expertise in IT, OT, and specific industrial processes. Regular training and simulations, such as attack simulations on cyber ranges, are essential for keeping the team's skills sharp. These simulations provide realistic experiences, allowing the team to practice their response strategies and refine their skills in a controlled environment, which is vital for preparing them to handle real incidents effectively.
Identification: Quick and accurate identification of potential cyber threats is pivotal in ICS/OT environments. This involves maintaining a detailed asset inventory, implementing network segmentation to limit the spread of threats, and continuous monitoring of systems to detect anomalies early. These steps enable the timely identification of unusual activities, which could indicate a cyber incident, thereby facilitating a swift response.
Containment: Once a threat is identified, containing it to prevent further spread is critical. This involves isolating affected systems and networks to limit the impact. Rapid isolation helps mitigate the threat while minimizing disruption to operational processes. Containment strategies must be carefully planned to balance security needs with operational continuity.
Eradication: Following containment, the next step is to remove the threat from the system. This can include patching vulnerabilities, restoring systems from backups, and eliminating malware. Eradication must be thorough to ensure that no remnants of the threat remain, which could lead to a resurgence of the issue.
Recovery: The recovery phase involves safely restoring operations and ensuring the integrity of the systems. This step is critical in ICS/OT environments where disruption can have significant consequences. The recovery process should include validation checks to ensure all systems are fully functional and secure before being returned online.
Lessons Learned: After an incident, conducting a thorough post-incident analysis is essential for learning and improvement. This analysis should evaluate what happened, how the response was handled, and what could be done better. Lessons learned should be incorporated into the incident response plan to improve the organization's cybersecurity posture and readiness continually.
Activities like attack simulations on cyber ranges are critical in ICS/OT environments due to their specialized nature. These simulations help teams understand the unique challenges of these systems and develop targeted response strategies that are effective in real-world scenarios.
Challenges in ICS/OT Response
As security, ICS/OT, and IT professionals, we must recognize the unique challenges these systems present and adapt our strategies to protect them continually.
By embracing the key elements of an Incident Response Plan – preparation, identification, containment, eradication, recovery, and lessons learned – we can ensure a robust defense against cyber threats.
This journey requires ongoing training, collaboration across disciplines, and staying informed about the latest threats and technologies. Let us collectively prioritize the security of our critical infrastructures, ensuring their safety and resilience for the future.
As professionals in this field, your expertise, vigilance, and proactive engagement are vital in safeguarding our essential services and the communities they serve.
About TAG
TAG is a trusted next generation research and advisory company that utilizes an AI-powered SaaS platform to provide on demand insights, guidance, and recommendations to enterprise teams, government agencies, and commercial vendors in cybersecurity, artificial intelligence, and climate science.