Breach & Attack Simulation Versus Cyber Range Simulation Training
Breach & Attack Simulation Versus Cyber Range Simulation Training
Understanding the differences and how they complement each other
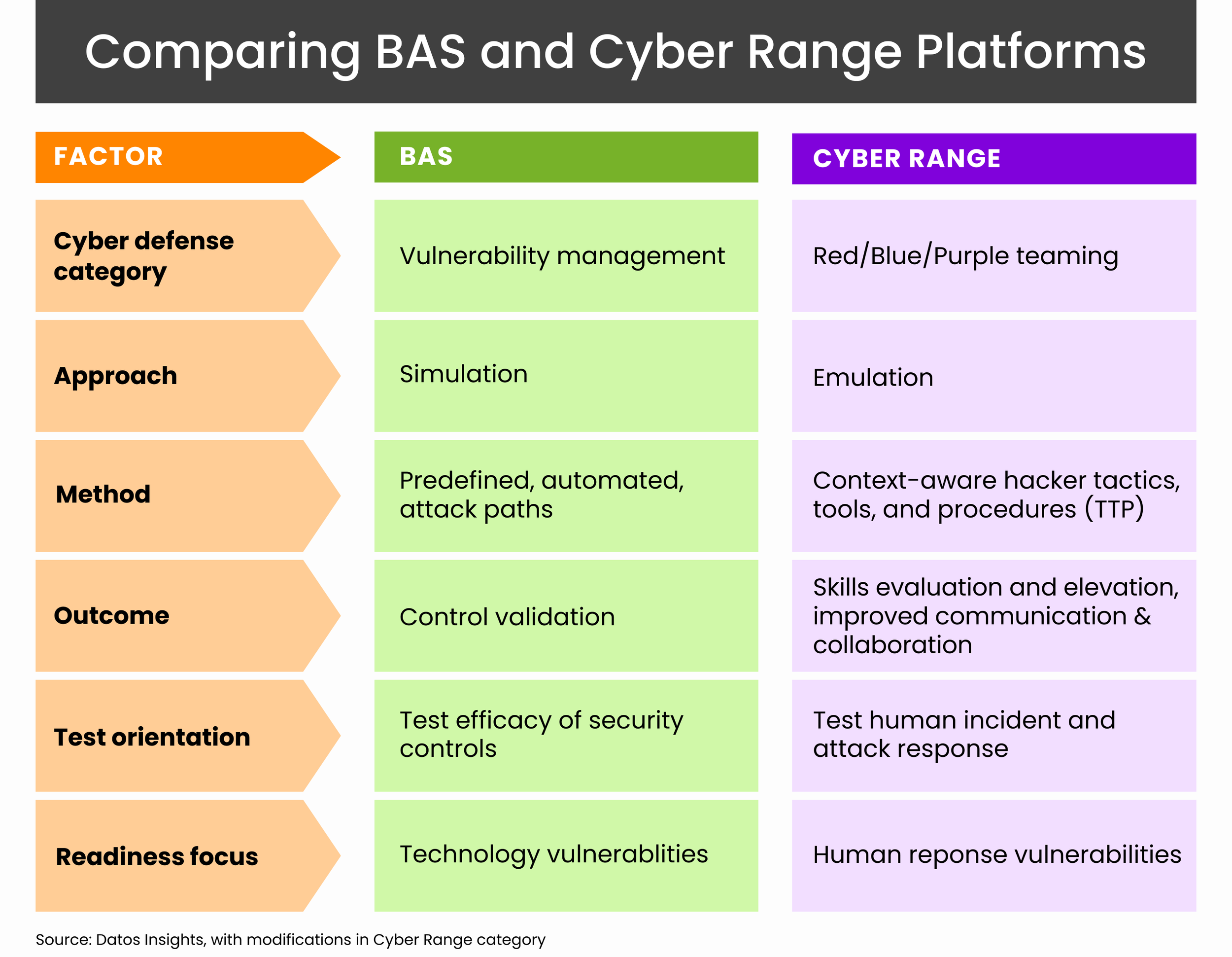
Breach and attack simulation (BAS) platforms and live-fire cyber range simulation training are both tools used to improve cybersecurity, but they serve different purposes.
BAS platforms are used to continuously probe and test an organization’s technological defenses–firewalls, anti-virus programs, EDRs, etc.–to identify vulnerabilities. It answers the question “How do we know our tools work?”
Cyber range simulation training focuses on the human element, providing cyber practitioners with realistic, immersive environments to sharpen their skills in defending against cyber attacks. It answers the question, “How do I know my people know what to do?”
On the one hand, you're fortifying your technology security. On the other, you're reinforcing your cyber defense team. Both elements are essential. You can’t clap with just one hand.
How do BAS platforms work?
BAS platforms simulate cyber attacks on a network or system to assess the effectiveness of security controls. The platform starts by scanning the network to identify and map out the systems and devices that are present. Once reconnaissance is complete, the platform will launch simulated attacks on the network, using techniques such as automated scripts, pre-configured attack scenarios, and manual testing to target the identified systems and devices.
As the simulated attacks – such as phishing, SQL injection, and malware payloads – are launched, the platform will track and analyze the results. This includes monitoring the network for any signs of compromise or attempted breaches and measuring the effectiveness of the network’s security controls. The platform will then provide a report on the results, highlighting vulnerabilities and recommending steps to remediate them.
One key benefit of using a BAS platform is that it allows organizations to test their security posture in a safe, controlled environment, without risking any actual damage to their systems or data. This can help organizations identify and address vulnerabilities before they can be exploited by real-world attackers.
Yet, BAS is only looking at technology. It’s critical to also ensure your people are also prepared for cyber attacks, since they are your last line of defense.
How does live-fire cyber range training work?
Cloud Range’s live-fire cyber range simulation training simulates actual cyber attacks in a controlled environment. It provides incident response and security teams with hands-on experience in responding to real-world cyber threats, allowing them to practice their incident response skills in a safe and realistic setting.
The training begins with a simulated real cyber attack on Cloud Range’s virtual network. The participants, such as security analysts, incident responders, and network administrators, are then tasked with identifying, containing, and mitigating the simulated attack.
During the training, participants use a variety of tools and techniques to respond to the simulated attack, such as analyzing log files, running forensic analysis, and implementing countermeasures. The training is designed to be as realistic as possible, including real security tools — SIEMs, EDRs, IDSs and more — as well as tactics used by actual attackers such as malware payloads, phishing attempts, and other attacks based on the MITRE ATT&CK Framework.
Cloud Range’s simulation training is led live by expert instructors who provide guidance and feedback throughout the exercise. After the exercise is complete, the instructors debrief the security leader, discussing what went well, what went wrong, and what could be improved for future exercises.
Live-fire cyber range simulation training gives cybersecurity teams practical experience they can’t get anywhere else (outside of actually being in a live attack, which is not the time to figure things out for the first time). It builds your team’s readiness and confidence to respond to real attacks.
Additionally, simulation training provides you with an understanding of the strengths and weaknesses of your current incident response plan, so you can modify it accordingly.
How do BAS platforms and live-fire cyber range simulation training complement each other?
BAS platforms help find weak spots in an organization's digital systems, and cyber range training prepares teams to respond effectively to cyber attacks. When used together, they strengthen an organization’s cybersecurity by identifying and remediating both technical and human vulnerabilities.
For example, you could use a BAS platform to spot network weaknesses and then engage in a mission on the cyber range that simulates a realistic attack scenario targeting those weaknesses. The exercise equips your team with hands-on experience in responding to actual threats that the organization is likely to face, enhancing their readiness for real-world attacks.
Combining BAS and cyber range simulation training benefits your organization's digital infrastructure and security team. By using both, organizations can gain a more complete understanding of their security posture and improve their ability to protect against cyber threats.
Learn more about Cloud Range’s full-service, live-fire cyber range simulation training. Contact us to see a demo!